Although the risks are generally well understood, the sheer volume and diversity of IoT devices requires a greater level of attention and control than a business might otherwise exercise.

Although the risks are generally well understood, the sheer volume and diversity of IoT devices requires a greater level of attention and control than a business might otherwise exercise. The most detrimental risk of IOT enviroments include the following: Inability to discover all IoT devices. IoT tools and practices must be capable of discovering and configuring all IoT devices in the environment. Undiscovered devices are unmanaged devices and can provide attack vectors for hackers to access the network. In a broader sense, admins must be able to discover and control all devices on the network. Weak or absent access control. IoT security depends on the proper authentication and authorization of each device. This is strengthened by each devices unique identifier, but its still important to configure each IoT device for least privilege -- accessing only the network resources that are essential. Reinforce other security measures by adopting strong passwords and enabling network encryption for every IoT device. Ignored or overlooked device updates. IoT devices can require periodic updates or patches to internal software or firmware. Ignoring or overlooking a device update can leave IoT devices susceptible to intrusion or hacking. Consider update logistics and practices when designing an IoT environment. Some devices might be difficult or impossible to update in the field and might even be inaccessible or problematic to take offline. Poor or weak network security. IoT deployments can add thousands of devices to a LAN. Each new device opens a potential access point for intrusion. Organizations that implement IoT often implement additional network-wide security measures, including intrusion detection and prevention systems, tightly controlled firewalls and comprehensive antimalware tools. Organizations might also opt to segment the IoT network from the rest of the IT network. Lack of security policy or process. Policy and process is vital for proper network security. This represents the combination of tools and practices used to configure, monitor and enforce device security across the network. Proper documentation, clear configuration guidelines and rapid reporting and response are all part of IoT and everyday network security. There is no single ubiquitous approach to designing and implementing an IOT infrasturure. But there is a common suite of considerations that can potentially help organizations check all the boxes to successfully architect and deploy an IoT project. Important implementation considerations include the following: Network connectivity. IoT devices can offer several alternatives for connectivity, including Wi-Fi, Bluetooth, 4G and 5G. Theres no rule that requires all devices to use the same connectivity, but standardizing on one approach can simplify device configuration and monitoring. Also decide whether sensors and actuators should use the same network or a different one. IoT hub. Simply passing all IoT data directly from devices to an analytics platform can result in disparate connections and poor performance. An intermediary platform, such as an IoT hub, can help organize, preprocess and encrypt data from devices across an area before sending that data along for analytics. If a remote facility is IoT enabled, a hub might gather and preprocess that IoT data at the edge before sending it along for further analysis. Aggregation and analytics. After the data is collected, it might drive reporting systems and actuators or be gathered for deeper analysis, query and other big data purposes. Decide on the software tools used to process, analyze, visualize and drive ML. One example includes the choics of IOT database and database architectures - SQL vs. NoSQL or static vs. streaming. These tools might be deployed in the local data center or used through SaaS or cloud providers. Device management and control. Use a software tool capable of reliably servicing all the IoT devices deployed throughout the IoT projects lifecycle. Look for high levels of automation and group management capabilities to streamline configuration and reduce errors. IoT device patching and updating is emerging as a problem, and organizations should pay close attention to update and upgrade workflows. Security. Every IoT device is a potential security vulnerability, so an IoT implementation must include a careful consideration of IoT configuration and integration into existing security tools and platforms (such as intrusion detection and prevention systems and antimalware tools). The future of IOT can be difficult to predict because the technology and its applications are still relatively new and have enormous growth potential. Still, its possible to make some fundamental predictions. IoT devices will continue to proliferate. The next few years will see billions of additional IoT devices added to the internet, fueled by a combination of technologies, including 5G connectivity, and countless new business use cases emerging across major industries, such as healthcare and manufacturing. Coming years should also see a reevaluation and increase in IoT security, starting with initial device design through business selection and implementation. Future devices will incorporate stronger security features enabled by default. Existing security tools, such as intrusion detection and prevention, will include support for IoT architectures with comprehensive logging and active remediation. At the same time, IoT device management tools will increasingly emphasize security auditing and automatically address IoT device security weaknesses. Finally, IoT data volumes will continue to grow and translate into new revenue opportunities for businesses. That data will increasingly drive ML and AI initiatives across multiple industries, from science to transportation to finance to retail.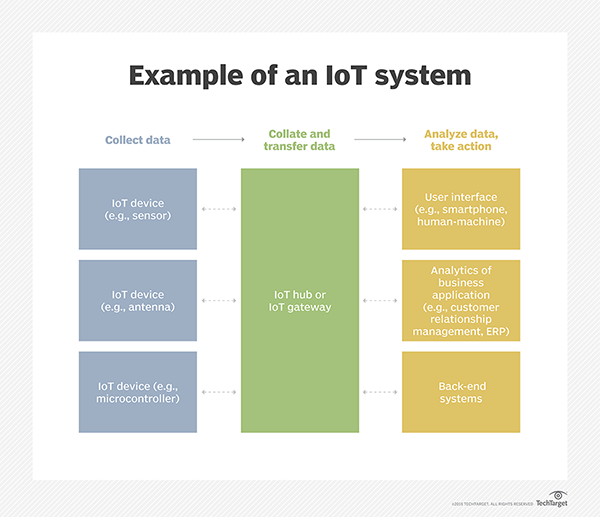 An example of how an IoT system works from collecting data to taking action
An example of how an IoT system works from collecting data to taking actionSTEPS FOR IMPLEMENTATION
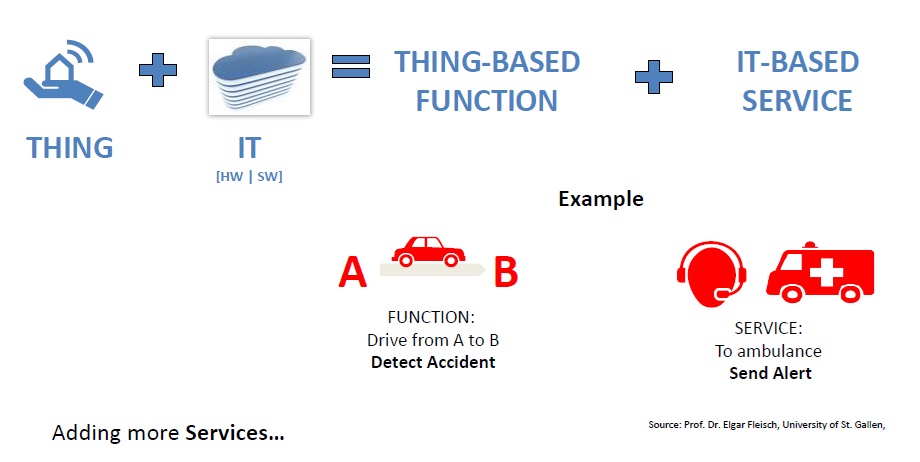
WHAT IS THE FUTURE OF IOT?

 Best resource for Online free Education
Best resource for Online free Education
