The entire concept of blockchain is a combination of a handful of different concepts and techniques i.e. a distributed ledger system, peer-to-peer network, key cryptography, hashing, and proof-of-work, etc.

1. Peer-to-peer Network
A peer-to-peer network is a decentralized and distributed network. In a P2P network, the participants nodes are not linked to a central body or server. Instead, all the nodes/computers are independent and are directly linked with one another to carry out transactions or information exchange. In a public blockchain, it is not necessary to know and trust each node in a network personally. The network and security are so designed such that authentic and legitimate transactions can take place even if the identities of sender and receiver stay anonymous. A peer-to-peer network is a secure network with direct contact between two nodes. A participant node of such a network has no geographical constraints, that is, it can be a part of the network from anywhere in the world.

2. Distributed Ledger System
Blockchain works on a distributed ledger system. By distributed ledger, we mean that the data record is not kept by any one central authority rather, it is available at every node of a P2P network. Every participant node in a network keeps updated copies of the data record or ledger in a blockchain. For instance, if you and I are two nodes in the Bitcoin public network, we both will have the same copy of the record of bitcoin transactions that took place till date. The record will not just show us our individual transaction but the transactions that took place between any two nodes in the network. This makes the entire network fraud-proof because everyone has a legitimate copy of the records and no one can falsify the transactions or double-spend the same bitcoins.
In every scenario, where blockchain is used, they adopt the same concept of the distributed ledger system.

3. Key Cryptography
Now, after understanding how a network is laid out to carry out transactions. The next natural question is of security of our data and the authenticity of participant nodes. If A wants to send a message or confidential information to B in a public network with hundreds of nodes, what is the guarantee that it reaches only B and not C? How can B assure that the message is coming from A? How can A and B both make sure that the message was not changed in the middle of transmitting?
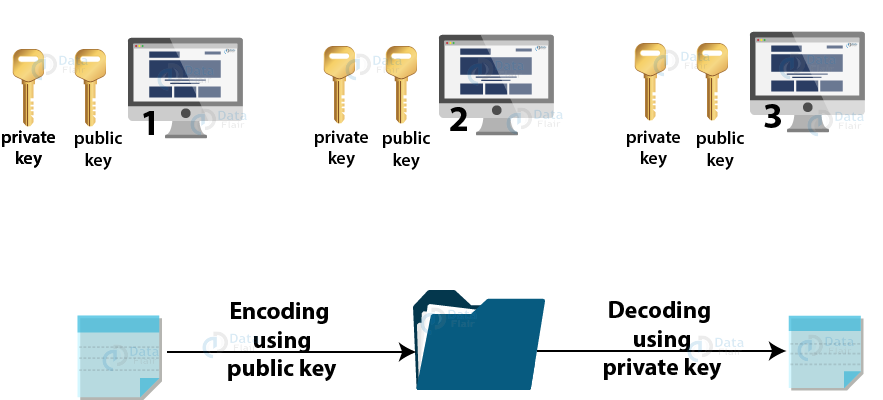
Well, the answer to every question and solution to this problem of security, data integrity, and user authenticity is “Asymmetric key cryptographyâ€. In such type of cryptographic arrangement, every node has two keys; Private key and Public key. The private key is known only to the node owner whereas the public key is known to all the nodes in the network. The combination of a private key and a public key makes a unique digital signature for every node. This makes the node authentic to carry out transactions and verifications. We will learn more about the cryptographic techniques in a separate post.
4. Hashing
Hashing is a non-reversible process of encrypting a blocks information. Every block in a blockchain is composed of a block header and transaction data. Hashing is encrypting an input value of variable length into an output of fixed length using SHA256 (Secure Hash Algorithm 256) algorithm. For instance, look at the image below to see how hashing encrypts a text value into a hash value. We will not go deep into the technicalities of the hashing algorithm as it is beyond the scope of our general discussion.

 Best resource for Online free Education
Best resource for Online free Education
